Removing the Dell Driver vulnerability

Posted on May 10, 2021 by Louise Howland
 News broke late last week about a security vulnerability which affects many Dell PC’s and Laptops (note not servers). The discovery has found a Dell driver vulnerability which affects hundreds of millions of PCs, notebooks and laptops which has been present yet remained hidden for the last 12 years.
Dell has apparently been releasing a firmware update driver for 380 of their PC models since 2009 that contains “five high severity flaws,” which has only just been discovered by an independent security research company called Sentinel Labs. Dell has immediately addressed the issue by issuing a security patch. It should be noted that there’s no evidence to date that the vulnerability is/has been exploited in the wild. An attacker would actually need local access to your machine in order to exploit the hack or trick the user via phishing or other means. On top of that, it would only affect a PC where the firmware has been updated, as the driver in question isn’t preloaded on PCs.
We have compiled simple to follow instructions for how to download Dell’s security update tool that will detect and automatically remove the vulnerability from your machine.
Please follow the link below to download the tool.
https://dl.dell.com/FOLDER07312946M/1/Dell-Security-Advisory-Update-DSA-2021-088_7PR57_WIN_1.0.0_A00.EXE
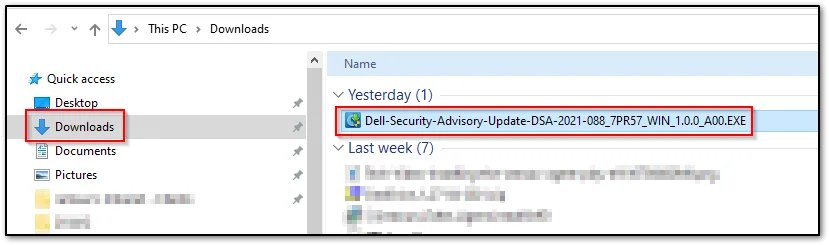
Open your downloads folder and double click on the file.
News broke late last week about a security vulnerability which affects many Dell PC’s and Laptops (note not servers). The discovery has found a Dell driver vulnerability which affects hundreds of millions of PCs, notebooks and laptops which has been present yet remained hidden for the last 12 years.
Dell has apparently been releasing a firmware update driver for 380 of their PC models since 2009 that contains “five high severity flaws,” which has only just been discovered by an independent security research company called Sentinel Labs. Dell has immediately addressed the issue by issuing a security patch. It should be noted that there’s no evidence to date that the vulnerability is/has been exploited in the wild. An attacker would actually need local access to your machine in order to exploit the hack or trick the user via phishing or other means. On top of that, it would only affect a PC where the firmware has been updated, as the driver in question isn’t preloaded on PCs.
We have compiled simple to follow instructions for how to download Dell’s security update tool that will detect and automatically remove the vulnerability from your machine.
Please follow the link below to download the tool.
https://dl.dell.com/FOLDER07312946M/1/Dell-Security-Advisory-Update-DSA-2021-088_7PR57_WIN_1.0.0_A00.EXE
Open your downloads folder and double click on the file.
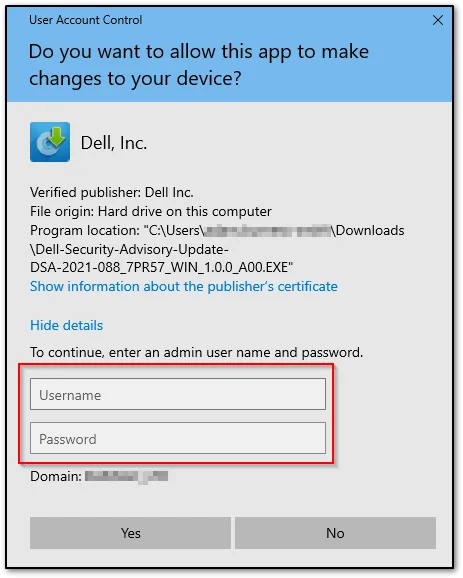
 When prompted either click “Yes” or enter a local admin account’s details so that the program can be given elevated rights.
When prompted either click “Yes” or enter a local admin account’s details so that the program can be given elevated rights.
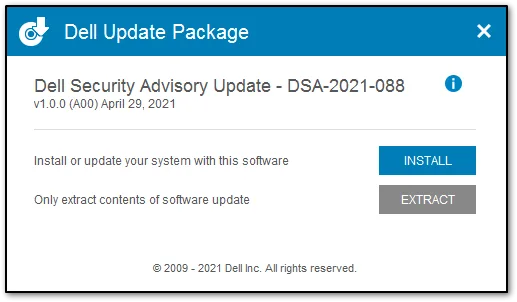
 When prompted please click on the “Install” button.
When prompted please click on the “Install” button.
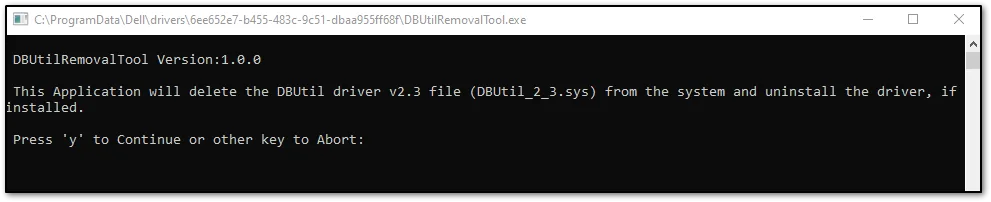
 This will trigger a black box to appear on you screen. Please enter “y” into the box to allow it to scan for the vulnerability.
This will trigger a black box to appear on you screen. Please enter “y” into the box to allow it to scan for the vulnerability.
 If the program detects any files with the vulnerability it will advise you and request you enter “y” again to confirm that the files can be removed.
If the program detects any files with the vulnerability it will advise you and request you enter “y” again to confirm that the files can be removed.
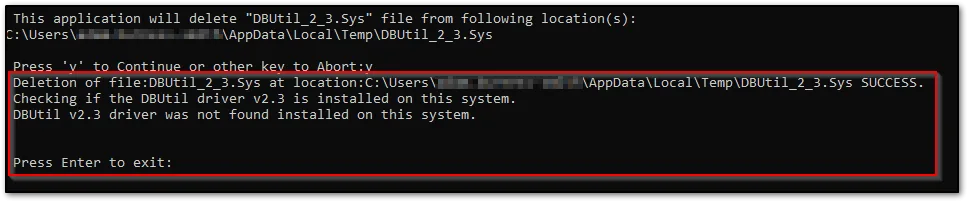
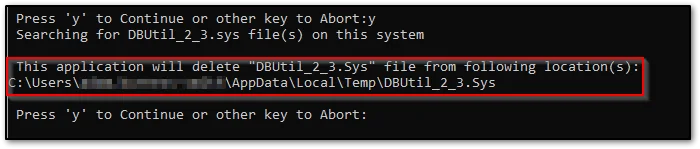 The program will then confirm the removal of the files and will ask you to press the “Enter” key to exit.
The program will then confirm the removal of the files and will ask you to press the “Enter” key to exit.
 We hope this helps. We’d love to talk to you about your specific IT needs, and we’d be happy to offer a no obligation assessment of your current IT set up. Whether you are at a point of organisational change, unsure about security, or just want to sanity check your current IT arrangements, we’re here to help.
We hope this helps. We’d love to talk to you about your specific IT needs, and we’d be happy to offer a no obligation assessment of your current IT set up. Whether you are at a point of organisational change, unsure about security, or just want to sanity check your current IT arrangements, we’re here to help.

Ensure your IT is at its strongest.
Take back control with ramsac’s free self-assessment tool that helps to strengthen your business’ IT systems.






