Passwords are no longer enough
Passwords alone are no longer sufficient to protect an organisation from cybercrime.
There are two main reasons for this, firstly users often do not take passwords seriously enough. They are either not complicated enough, or used for multiple accounts, or not changed frequently enough, or shared with colleagues or worse, all of the above. Secondly, password data is too frequently stolen. Cyber criminals have a host of ways of tricking you into entering your username and password into a trick website, or they steal batches of usernames and passwords in data hacks of third parties (such as the infamous breach of the British Airways system for example).
It’s fairly easy today, to login to the dark web and buy thousands of email addresses and passwords for next to no money. On the basis that at least some of your staff will use the same password for their BA account as they use for work, it’s just a numbers game for committed cyber criminals to gain access to your data. And don’t be fooled into thinking that no one is interested in your company activities – we see businesses and charities of all shapes and sizes, targeted week in, week out.
Why are passwords no longer enough?
We have more data in the cloud
With more and more businesses moving to cloud-based storage systems such as SharePoint, Box, Office365, Google Drive etc, there are less and less organisations requiring you to use a VPN to access company data. So, if all that lies between a cyber criminal and your precious data, is a weak password stolen in a spear phishing attack three months ago, you can understand why passwords are no longer enough!
What is Multi-factor authentication (MFA)?
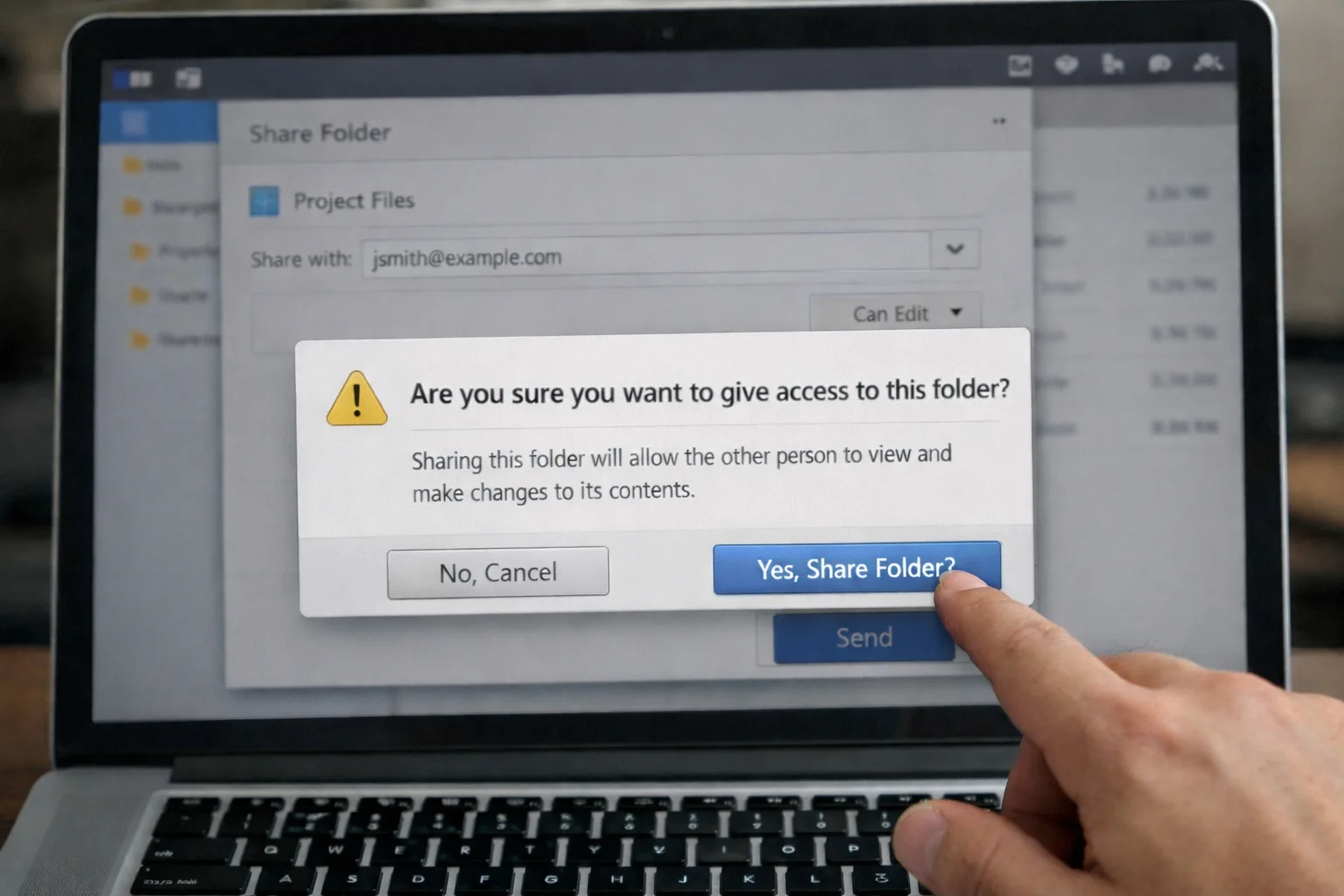
Multi-factor authentication (MFA) is the process of needing more than one piece of information to login to a secure website or service. In traditional systems, all you need to know to gain access to an IT system, is a user name and password. MFA introduces a second component, often a PIN code that can only be generated by a mobile phone (which in itself requires a PIN code, face or thumbprint recognition to open it) or an access token, meaning that for a malicious user to gain access to a system, they would need to steal not only your password information, but also your mobile device – making it significantly harder for access. MFA isn’t really new, we’ve been doing it at cashpoints for decades – to get money from your bank you have always needed both your password (your PIN) as well as the associated bank card.
Is MFA really a deterrent for cyber-crime?
The answer to this is yes, the rate of compromise of accounts using any type of MFA is less than 0.1% of the general population, so 99.9% of cyber-crimes are prevented where MFA is being used. In extremely targeted attacks where attackers are willing to invest enough to break MFA, it is possible but attacks on Microsoft user accounts that are capable of bypassing MFA are so rare Microsoft don’t actually have any stats on them. “Compared to password attacks, attacks which target non-password authenticators are extremely rare,” said Alex Weinert, Group Program Manager for Identity Security and Protection at Microsoft.
MFA and Office 365
Due to the rapid adoption of Office 365, it has become a prime target for hackers. National Cyber Security Centre (NCSC) issued a report stating they were aware of several incidents involving the compromise of O365 accounts within the UK, including the use of such methods in targeted supply chain attacks. Once a hacker has obtained the users credentials, not only can the account access be used to access documents across a user’s O365 surface (SharePoint, OneNote etc.) but it can also be used as a launchpad to carry out further compromises within an organisation.
By adopting MFA organisations will radically reduce this cybersecurity risk. Office 365 support various different MFA mechanisms depending on the subscription, giving organisations flexibility over the mix of MFA measures they can implement.
Organisations who are still relying on passwords as their primary means of cybersecurity protection are leaving themselves vulnerable to an attack. If you would like to discuss MFA and how it can increase cybersecurity protection for your organisation please call us on 01483 412040