How to spot a phishing email

Posted on February 12, 2020 by Louise Howland
Can you identify a phishing email from the real thing?
A phishing email is a fraudulent email that attempts to scam you by looking like an email from a legitimate business or person. A phishing email tries to get you to let your guard down and give access or information to cyber criminals. They are often designed and written in a way that looks like an official email that requires urgent attention. Good phishing emails look like the real thing. So how do you spot one?How to Spot a Phishing Email
- Check the address and subject line
- Be suspicious of untidy design
- Look out for spelling mistakes
- If it’s too good to be true, it probably is
- Consider context. Were you expecting this email?
- Compare if you can
An example of an Apple phishing email
A few years ago, I received an invoice from Apple for something I hadn’t purchased. My immediate reaction was panic. I thought someone had hacked into my Apple account, and now they were happily spending my money. But, as I hovered over the cancel subscription link on the email, something made me pause and take a second look. On the face of it, it looked like an email from Apple, but as soon as I looked a little deeper I noticed more and more things that didn’t add up. My cybersecurity awareness training kicked in and I realised it was a phishing email. This is the phishing email that was sent to me. Check out the differences between a legitimate email from Apple Inc. and a phishing email from a hacker masquerading as Apple Inc. *Please note that I have blurred out my personal details in all images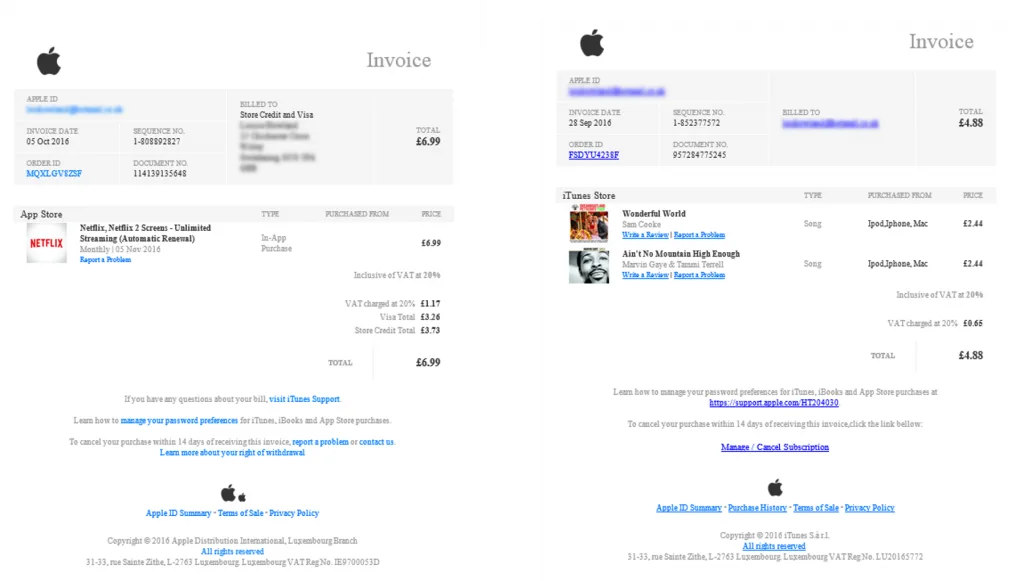 On the left is the real invoice from Apple and on the right is the phishing email. On the surface they look very similar but I found nine differences.
On the left is the real invoice from Apple and on the right is the phishing email. On the surface they look very similar but I found nine differences.
1. The address and subject line
The address the email came from was suspicious and the subjects were different.
2. Email design and styling
On the legitimate Apple email all the hyperlinks are in light blue with no underline. In the phishing email they are a darker blue and all underlined.
3. My details
On the real Apple email they list my email address and home address. The phishing email only has my email address – as I assume the hackers don’t know my home address.
4 & 5. Changes from the usual email layout
On the real Apple email there is a hyperlink to use if you have questions about your bill. This sentence is missing completely from the phishing email.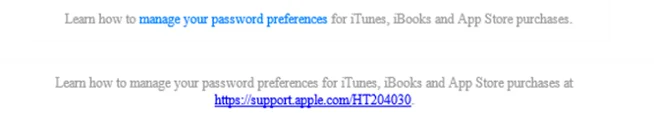
6. Spelling errors
This is lazy even for a hacker; spelling errors are an obvious red flag. Normal emails are proofread and carefully edited. Phishing emails are not.
7 & 8. Limiting contact options
Firstly, the wording around cancelling your purchase on the real email is very different from the phishing email. Apple offers you three links to click to contact them. The phishing email gives you one. In simple terms, this increases the likelihood that you will click it.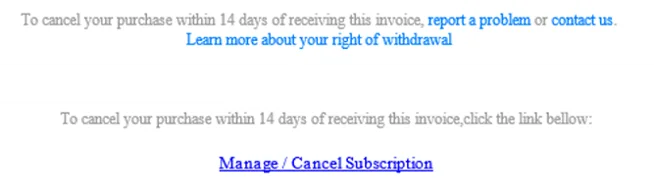 Secondly, the hyperlink for ‘Manage/Cancel Subscription’ on the phishing email is different from all the other hyperlinks.
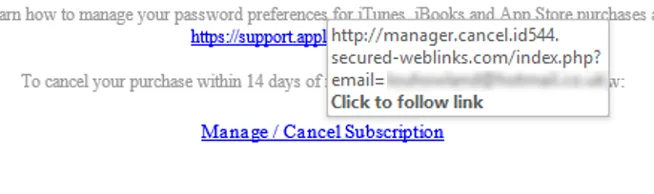
I didn’t click on the link for obvious reasons but I assume it would take you to a page that either encourages you to enter personal details (possibly including payment information) or it could be a malicious link that releases a virus onto your machine.
See below for what the link looked like when I hovered over it.
Secondly, the hyperlink for ‘Manage/Cancel Subscription’ on the phishing email is different from all the other hyperlinks.
I didn’t click on the link for obvious reasons but I assume it would take you to a page that either encourages you to enter personal details (possibly including payment information) or it could be a malicious link that releases a virus onto your machine.
See below for what the link looked like when I hovered over it.
9. The Apple logo
The last obvious difference I could see was the second Apple logo which was different on the two emails. Left is real, right is phishing.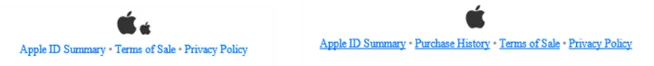
Knowing how to spot phishing scams
At first glance this email was very convincing, it really takes a trained eye to spot the difference – these are far more sophisticated than emails from Nigerian Princes seeking to move £10m out of the country! Once I delved a little deeper there were actually quite a few signs the email was not legitimate. Other phishing emails may only have one or two clues, so it is vital you are always vigilant when looking at your emails and if something doesn’t feel right, don’t click on it. In 2020, phishing is becoming an increasing threat because of cyber criminal’s access to machine learning systems. This sophisticated technology means that phishing emails have become an automated process, meaning they are increasingly accurate and therefore believable. It’s thought that 2020 will see more phishing emails masquerading as:- PayPal. There have been reports of PayPal users receiving email pertaining to ‘unfamiliar log-ins’ that request the user clicks a link to confirm their identity.
- Employers. Some cyber attackers have sent emails to employees that look like they are from their company’s HR team, asking them to click a link to solve a problem with their salary payment.
- Banks. The Hong Kong Monetary Authority have recently sent out an email warning HSBC account holders of a phishing email containing a link to an ‘e-Advice’ note detailing a recent payment.

Ensure your IT is at its strongest
Take back control with ramsac’s free self-assessment tool that helps to strengthen your business’ IT systems.







