Cybersecurity guide: how accounting firms should anticipate risks

Posted on July 2, 2021 by Louise Howland
Accounting firms hold special categories of data, and a lot of valuable data at that. With many security breaches (67%) happening due to user error, cybercrime has never posed a greater threat.
Professional accountants, and accounting firms, often store, manage, and oversee valuable financial data. They are key individuals entrusted with potentially sensitive business data. As this kind of information passes their desk often, whether requested by a client or for simple admin, these professionals need to take extra precautions.
Accounting is a very sensitive industry, open to cyber-attacks. So, how can accountants protect themselves?
Be risk aware
Much like physical risks, a cybersecurity risk assessment should be carried out to help understand where your risks are.
This may seem daunting, or even complicated, but it is a valuable exercise and a strong starting point for identifying areas of risk. Weaknesses are not always where you think, which is why we’ve created an IT health assessment to help identify areas of your security to strengthen.
Conducting a self-risk-assessment will equip you with the essential knowledge of where your risks are, and how you can control them. Some risks, like outdated computers, can be easily fixed; whereas other risks, such as human errors, are harder to control without training and sharing the right knowledge.
Cybersecurity concerns for accountants
As accountants store sensitive and valuable data, there are many security concerns. These could include:
1. Databases getting sold on the dark web
2. Customers receiving emails pretending to be legitimate and from an accounting firm
3. Unwanted or unauthorised access to systems
4. Data being locked behind a ransomware paywall
5. A bug hiding in a system for a long time, allowing for malicious data collection
Whilst the list of cyber-related risks and threats are becoming even more sophisticated, anything that compromises the integrity of the service that you provide is a risk that needs addressing. But what can you do to ensure you keep your employees and customers safe?
Protecting accounting firms from risks
There are some basic procedures you can put in place to assist in your steps to becoming cybersecure.
1. Regularly train your staff
As mentioned, 67% of breaches and hacks are due to human error or a password being compromised. Educating your team regularly on the different (and changing) aspects of cybersecurity is critical. This training should include advice on how employees can ensure safety when online or handling sensitive data.
Accountants should consider the following areas for cybersecurity:
– Good password health, and avoiding using the same password for multiple accounts (which is called ‘daisy chaining’)
– Storing passwords in unsecure places, such as in web browsers
– Avoid using unsecured networks for work, such as coffee shops
2. Keep systems up to date
Ensure all computers are up to date, especially operating systems and any software updates or patches. In 2017, two separate attacks exposed billions of details across various industries by hacking older versions of Windows that no longer received security updates.
Regularly applying security updates, including patches, is a small and convenient step that accounting firms can take to ensure greater security and protection against risk varieties. This means evaluating what software is being run by your computers, especially if any are taken off-site, and ensuring that software is patched.
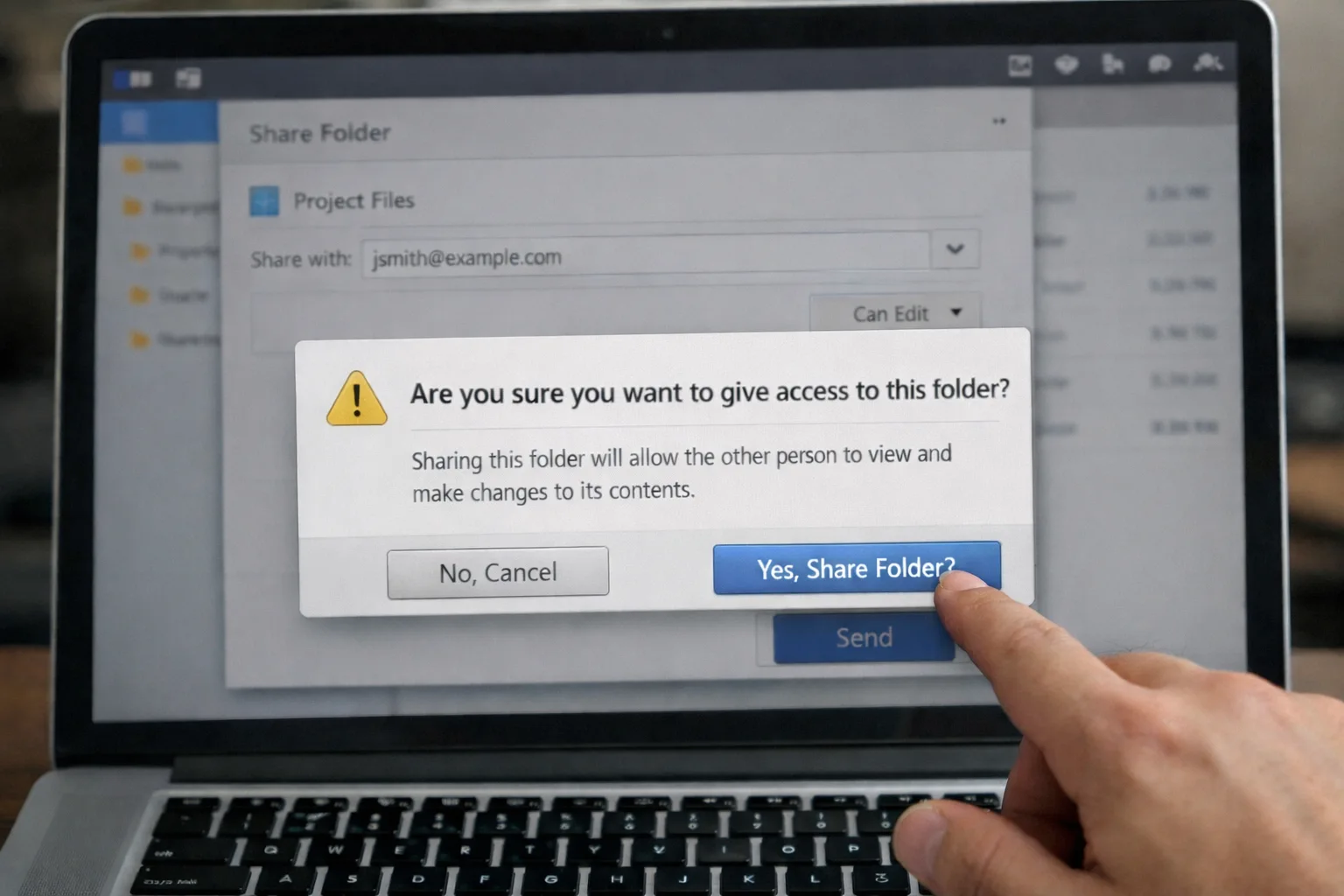
3. Manage levels of access
In a busy office environment, such as an accounting firm, giving all staff the ability to access data is a vulnerability. For example, admin staff may not need to see more confidential data such as financial statements. You should actively manage access to different kinds of data, ensuring that there’s a reasonable chain of authority.
Regulating access levels, like setting up file permissions, can help to isolate any potential breaches and risks.
4. Setting up multi factor authentication
By having more than one step to login to software, you can prevent potential hackers and other malicious users. This can be achieved via an authentication app on your phone, using a mobile phone number to get a temporary access code or having to use a USB stick as a ‘key’. With its extra layers of security, this is known as ‘multi-factor’ authentication.
The more steps and alternative ways there are to access an account the better for your security.
ramsac can help you change the way your business thinks about cybersecurity. Speak to us today about how we can help your accounting firm stay secure.