One of the great benefits of SharePoint is the ability to collaborate and share files and folders with people from outside of your organisation, as well as the colleagues you work with internally. However, if not done properly, sharing content externally can be a major security risk, putting your data in jeopardy if it falls into the wrong hands.
The goal with external sharing is to balance enough user freedoms to collaborate with those outside of your company, but to encourage data protection and security at every step. This means that if you’ve got a client that needs to access files, you can make the most of Microsoft’s modern workplace tools like SharePoint to ensure that secure collaboration with the right people happens regardless of where they work, but that you retain control to ensure you’re not sharing any more than you mean to.
Here’s everything you need to know about external sharing in SharePoint.
What is external sharing?
External sharing describes the process of sharing content, such as files, from within SharePoint to a user who is outside of your company.
For those making the most of Microsoft 365’s intuitive applications, SharePoint is the main tool when it comes to document management, sharing, and storage. This is important because many of the configurable permissions, when it comes to external file sharing, are controlled through SharePoint’s admin centre.
Even though external collaboration can happen across different Microsoft 365 solutions, including OneDrive and Teams, SharePoint is considered the most central way of doing this.
The difference between sharing and access in SharePoint
Sharing is one of many ways to allow external users to access files and resources from inside your organisation. If your work requires collaboration, understanding these different methods for authorising safe and secure file access can be critical.
External sharing is a way for a business to ‘share’ documents, files, or libraries. There are many possibilities for what you can share, including:
- compatible files, documents or similar
- photos, screenshots, and visuals
- entire folders and libraries from your OneDrive account
When different users need to collaborate, whether that’s continuous communication on chat apps like Microsoft Teams, or if you need to share calendars to schedule meeting time, granting access can make this process easier.
You can grant access to external users by adding them to a Microsoft 365 team, controlling what content is visible to different users.
Safe, secure sharing practices should be followed to ensure that sensitive and potentially confidential files and data doesn’t become compromised, stolen, or ransomed.

SharePoint external sharing
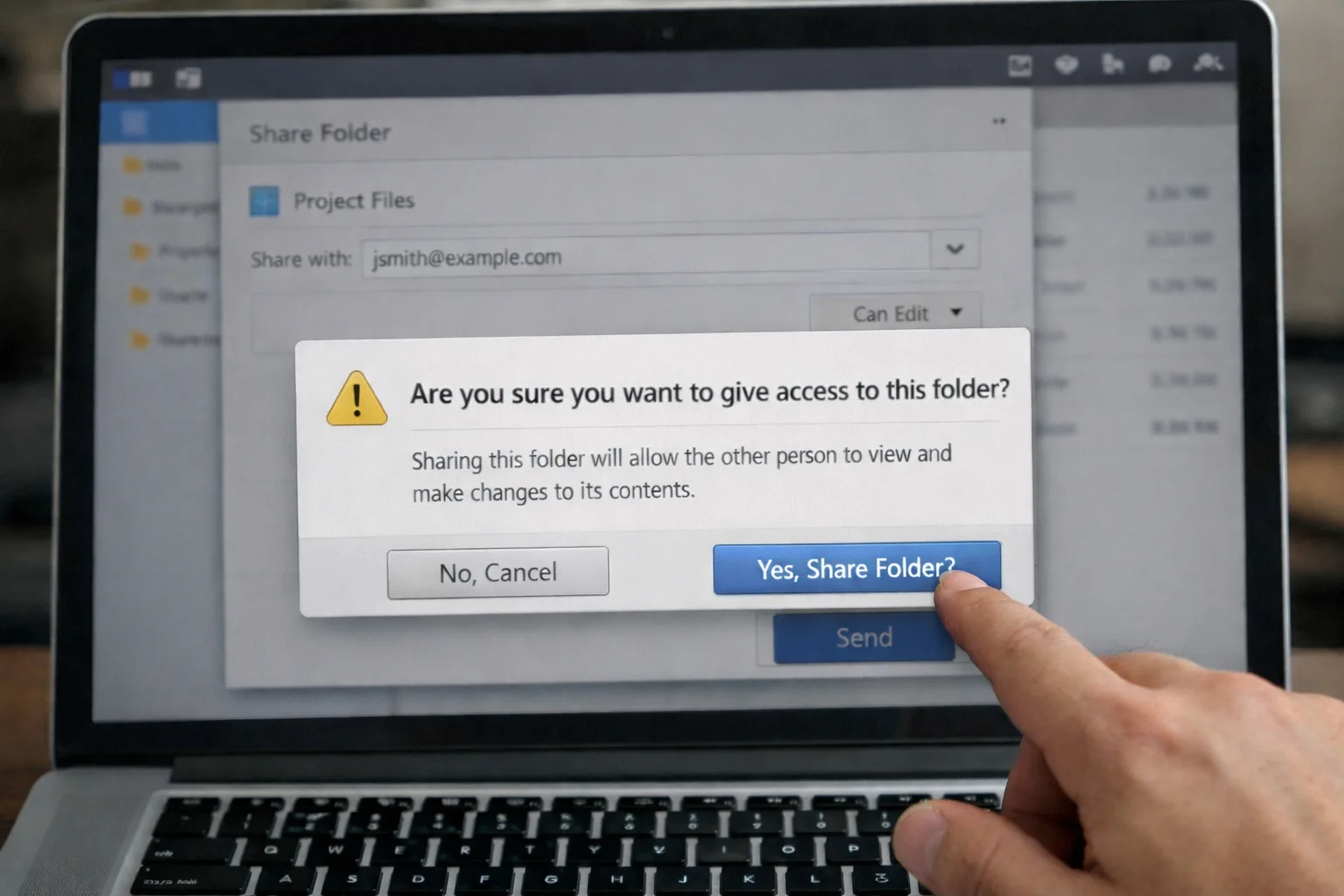
SharePoint external sharing and access settings can be restricted and controlled from the admin centre, which means security can be configured to different levels of users. This can be managed either at an organisational level, which is where admins can enable external sharing, or on a site level, where sharing rules can be established on a site-by-site basis. We always recommend sharing by Site, rather than by whole Organisation. In our case for example, we have a SharePoint site called ‘Client Shared Files’ and that site is enabled for external sharing. The naming convention makes it fairly obvious that this is a shared site and helps users to remember to avoid sharing confidential data on that site, thus reducing the risk of a user accidentally sharing a folder that contains all the company’s best kept secrets!
It’s important to remember external sharing settings must be enabled at an organisational level first, before changing the rules for different sites. Only a Global or SharePoint admin will have the authority to change these settings, where site owners will have a limited role and won’t be able to effect external sharing for the most part.
You can set up unique rules in SharePoint, changing whether content can even be shared with different types of recipients– this means the different guests.
Existing guests
If this option is selected from within the admin centre, it enables sharing only with people already in your Azure Active Directory, which is an identity and access management solution.
New and existing guests
This option, again located in the admin centre, opens the invitation to new guests as well as contacts already existing in your Microsoft Azure Active Directory. Under this rule, users can share files, images, and documents.
Any guests receiving shared content can expect an email invitation first, which will have a link that directs them to a file or document.
Guests will be required to sign in to view content and they will leave a footprint in your Azure Active Directory, meaning that they are remembered and assigned similar permissions to other users. This allows you to keep a level of control over who has access, enabling you to restrict a given user at any stage.
Anonymous sharing
This option enables anonymous sharing with any user. We would always encourage organisations to restrict this ability, as it really is the widest possible share and the most prone to abuse. There are very few organisational reasons to allow this level of open sharing.
With anonymous sharing. a link will be generated once content is shared externally and then any user can use it to edit, review and work on transferred files or documents. The problem with this type of sharing, is that link can be sent to anyone, at any time and you can’t control who can use it – so you really have opened up everything in that site to anyone who later gets hold of the link. If you’re using this level of sharing you’ve really only got to be storing data that you would be happy to have published to your public facing website, because the security is essentially the same.
Securely sharing with different users in SharePoint
External sharing is critical when it comes to collaborating with different users, either those inside your organisation, or those outside of it. But when it comes to safely and securely sharing your work, it’s advisable to use authenticated external users rather than anonymous ones.
If a file is shared anonymously, and the end user hasn’t been verified, then there will always be a risk that data can be forwarded and accessed maliciously. The best method to prevent your files getting into the wrong hands is to authenticate users, which helps to establish some trust with those who will be receiving your documents and libraries.
Get SharePoint advice from the experts
SharePoint is an intelligent hub for a company’s files, news and more. If you’re wondering how SharePoint can be utilised better to support your busy teams, then get in touch the specialists at ramsac today.